Just as everything has changed since the mid-nineties when the internet started, so too have phishing attacks. I’m sure you remember getting those Nigerian Prince scams or a widow asking you for help a while back? Well, those scams simply seeking money are not by any means the same as they are today (and to become in 2019).
You see, as people started expecting more from the internet, so too have the attacks gotten more sophisticated and deceptive. They are more creative and have become especially difficult to recognize.
In fact, cybercriminals have gone past simply sending out emails (although they still are using email to get onto your network) getting into texting and social media to help them be more effective and more targeted at deceiving your users.
They are beginning to recognize how to leverage context—social context, relationships, holidays, etc.—to trick users to give over valuable information, let their guard down, or even grant hackers access to your network and your data.
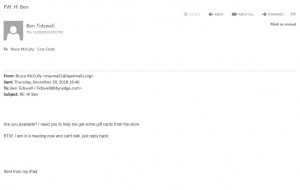
Take this recent attack for instance. This was a phishing attack that hit some of my team members last week.
A scammer used a completely fake email to ask a very simple request.
First off, there are some red flags here. The subject line is completely out of character for me. Second, the From address myemail@ipademails.com sounds a little phishy. Third, my asking Ben to purchase and scratch physical gift cards is out of character for me. This scammer could have done a little more homework and might have had a better chance at deceiving someone.
Unfortunately for this scammer, my team is highly skeptical of requests like these and they know me better than to make a bogus request for gift cards. And I’m sure that many of your team members would be able to see through this scam as well (if you’re in doubt, consider refreshing their memories on how to avoid a scam).
Unlike many previous scam attempts, scammers are searching for relationships through social media (Facebook, LinkedIn) and are trying to leverage those relationships to get through to your users. They know that many people will open emails from folks they recognized (they definitely will click on their email).
Their next milestone will be for your users to take action—click on a link or follow through with a money wire. My message to you: it only takes one.
Just one user needs to pull the trigger on the request to have paid off big time.
Some of the most common phishing attacks are aimed at getting your victim’s username and password. They have a subject line that entices someone to click, a recognizable name in the From line of the email.
Most commonly, these scammers evoke a few emotions:
- Curiosity—no one expects others to have specific information on them. They become curious as to what the email is about and click on it.
- Fear—if your users perceive a terrifying threat, they are likely to act quickly and irrationally. Instead of thinking about a request, you’re probably going to see them reacting instantaneously to the request (most often complying with what was asked of them).
- Trust—someone sending scam emails is definitely interested in getting your user to trust them enough to share their passwords or send them valuable information. These criminals are getting better at getting folks to trust and comply with their requests.
The bottom line: no matter how much security (and specifically cybersecurity) improves in the future, there will always be a vulnerable element on your network: humans.
What can you do to keep safe?
Just like every coach reinforces with every player of his or her team—stay on your toes. If you’re flat-footed, you’re going to be too slow to react. Even if you cannot predict what’s going to happen tomorrow, being agile and expecting cybercrime is a good first step to recovering from it. Note: part of being on your toes is knowing where your vulnerabilities lie and prioritizing ways to shore up your network security. Experts recommend getting a ransomware vulnerability assessment to help address network security issues.